Internal user attempting to connect to the Internet through the firewall.
Physical layer - ingress interface
Data Link Layer/Ethernet
Inspect Driver [inspect Engine]
Network Layer/IP Routing
Inspect Driver
Data Link Layer/Ethernet
Physical layer - egress interface
Opening an SSH connection to the firewall itself
Physical layer - ingress interface
Data Link Layer/Ethernet
Inspect Driver
Network Layer/IP Routing
Transport Layer/TCP connectivity
Layers 5-7/SSHD process
Data Link Layer/Ethernet
Inspect Driver [inspect Engine]
Network Layer/IP Routing
Inspect Driver
Data Link Layer/Ethernet
Physical layer - egress interface
Opening an SSH connection to the firewall itself
Physical layer - ingress interface
Data Link Layer/Ethernet
Inspect Driver
Network Layer/IP Routing
Transport Layer/TCP connectivity
Layers 5-7/SSHD process
--------------------------------------------
Longer Version with more Functions Enabled on the FW module:
NIC hardware
-The network card receives electrical signalling from the link partner.
NIC driver
-Sanity checks
-The NIC hardware decodes the signal and passes it to the operating system's NIC driver via the PCI bus
-The frame is converted to an mbuf entry and the frame headers are stored for later use.
-NIC driver hands off the data to the operating system's mbuf memory space
Operating system IP protocol stack
-The OS performs sanity checks on the packet
-Hand off to SXL if enabled, or to Firewall Kernel if not
SecureXL (if enabled)
-SXL lookup is performed, if it matches, bypass the firewall kernel and proceed with (Operating system IP protocol stack, outbound side)
Firewall Kernel (inbound processing)
-FW Monitor starts here
-Connection state lookups, some protocol inspection, rulebase processing, antispoofing lookups etc
-Processing order can be seen via fw ctl chain
-Bypass complex inspection if not needed
Complex protocol inspection (AV is an example)
-Leave the kernel and process under userland.
-Enters back at this same stage if the traffic passed
(inbound processing stops here)
Firewall Kernel (outbound processing starts here)
-Route lookup
-Check Point sanity checks etc
-FW Monitor ends here
-Pass to operating system
Operating system IP protocol stack
-The OS performs sanity checks on the packet
-Pass the mbuf to the NIC driver for the appropriate outbound interface
NIC driver
-Tag the packet as an ethernet frame by adding MAC addresses for source and destination
NIC hardware
-The NIC hardware encodes the signal and transmits it via wire
----------
Between all the steps there are queues. These queues accumulate packets and on intervals flush them to the next step. All of this happens very very quickly in small CPU time slices.
The INSPECT engine itself is more to do specifically with protocol inspection rather than all of the other steps. INSPECT runs traffic against definitions, if the definitions match it usually means that it hit a protection and the appropriate action is to (drop, log) the traffic.
There are a LOT more steps in the sequence I posted above, for example any kind of VPN traffic gets different processing, which is done in chains. The chains look at the traffic type and determine the next step via a finite state machine.
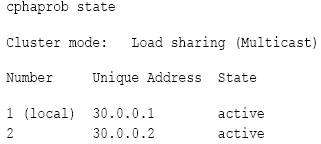
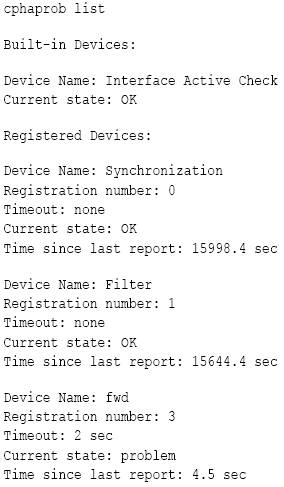
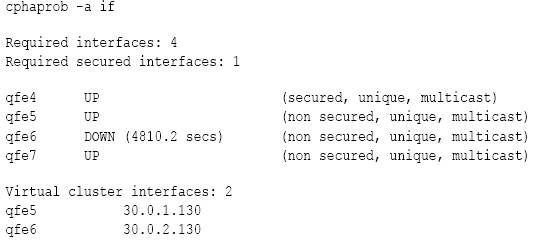

![[ike2.png]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgx9WaeLOCNBdwZov4DoylfDvbaQ7zGS84igAWw4XEl1Ak_M8Nrls1M1muMhg5iVqp3aF9-uCTkiUmun3dDe29k5-m1cjfCOqPKFGD0EA2gtVgp90PXYuj6XIeBOoB5zkuVrG1EActNPTta/s1600/ike2.png)